Ph0wn CTF 2023 - Teaser
Description
Posted on the Discord server.
🔥 Teaser
We’re a bit disappointed.
We’ve put something special on Ph0wn’s website since ~June and nobody has noticed yet! 🧐
Come on! Get ready hackers!
https://ph0wn.org/
Solution
1. Find the “something special”
From the message we know something has been put on the website since June.
I knew that ph0wn CTF had a Github page so I checked if there was a repository related to their website:
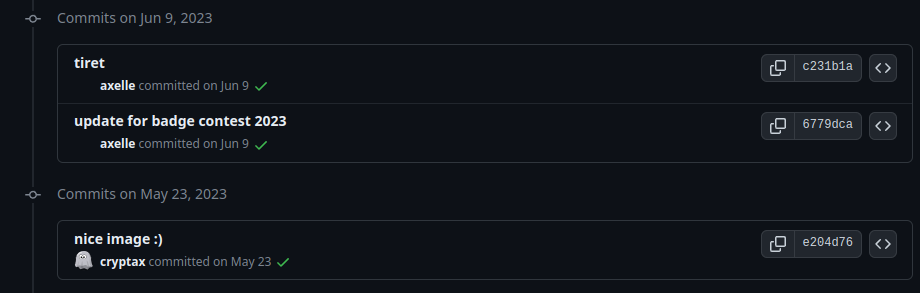
There is indeed a repository for the website. Then I checked the commit history to see if there was anything suspicious around June.
I found a commit with a very suspicious message:
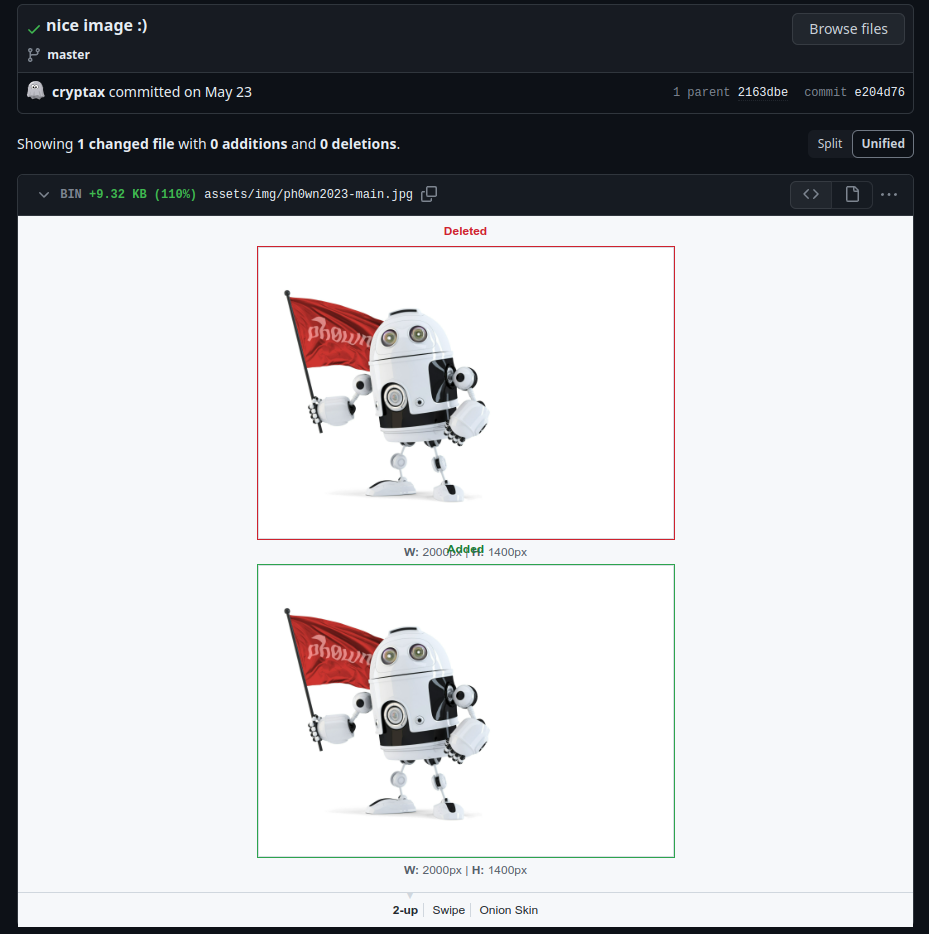
The commit added a picture visually identical to the previous one but has 9.32 KB more data:
There must be something hidden in the new picture, so I downloaded it and tried to find the hidden file inside the picture.
2. Extract the hidden file
I used Aperi’Solve to apply multiple steganography tools on the picture.
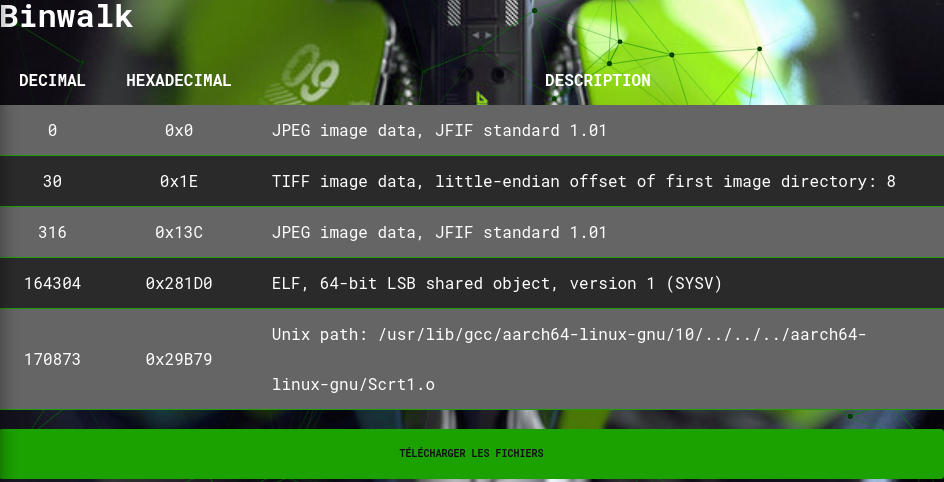
In the Binwalk section, we can see that there is an executable at the end of the file which should be the hidden file:
3. Binary analysis
The executable is an ARM 64-bit executable:
1
2
$ file 281D0
281D0: ELF 64-bit LSB pie executable, ARM aarch64, version 1 (SYSV), dynamically linked, interpreter /lib/ld-linux-aarch64.so.1, BuildID[sha1]=8c3971d6f371f35f21e07be9aea36133b62f3bfc, for GNU/Linux 3.7.0, not stripped
Using Ghidra, we can see that the executable prints an obfuscated string:
1
2
3
4
5
6
7
8
9
10
11
12
void main(void)
{
undefined auStack_b0 [168];
void *local_8;
memcpy(auStack_b0,&DAT_001009e8,0xa8);
local_8 = (void *)deobfuscate(auStack_b0,0xa8,0x23);
printf("%s",local_8);
free(local_8);
return;
}
We could deobfuscate it but since the program already prints the deobfuscated message, we just need to run it.
To run the ARM binary on a x86_64 Linux system, I followed this guide RUNNING ARM BINARIES ON X86 WITH QEMU-USER and got this output:
1
2
3
4
$ qemu-aarch64 -L /usr/aarch64-linux-gnu ./281D0
----- PDU---1/1 ------
001100098121436587F900000B3CC176589F769F43A0ECBB0E9A87EFA0343D046296E9A0FA1CB476BFEFA186028E86DDDD1BD4BDDC92B6EEE1343DED3EB768ADEA2605
Length: 66
4. PDU
After some research, the PDU from the message seems to mean Protocol data unit.
I search for any Github project related to PDU on Google and I found that it can be decoded:
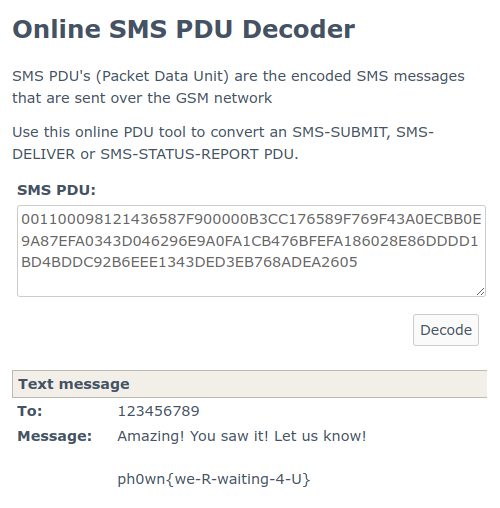
Then I search for a PDU decoder and the first result was about SMS PDU Decoder/Converter.
I used this tool to decode the message:
and here is the flag: ph0wn{we-R-waiting-4-U}.