TFC CTF 2023 - SOME TRAFFIC
Description
- Category:
Forensic
Our SOC analysts said that in the last few days, some of our employees started to upload a lot of photos on random sites. Check it out.
Flag Format: TFCCTF{…}.
Disclaimer (forensics+stegano)
Download:
Resolution
We have the file sus.pcapng1 which contains network packet capture.
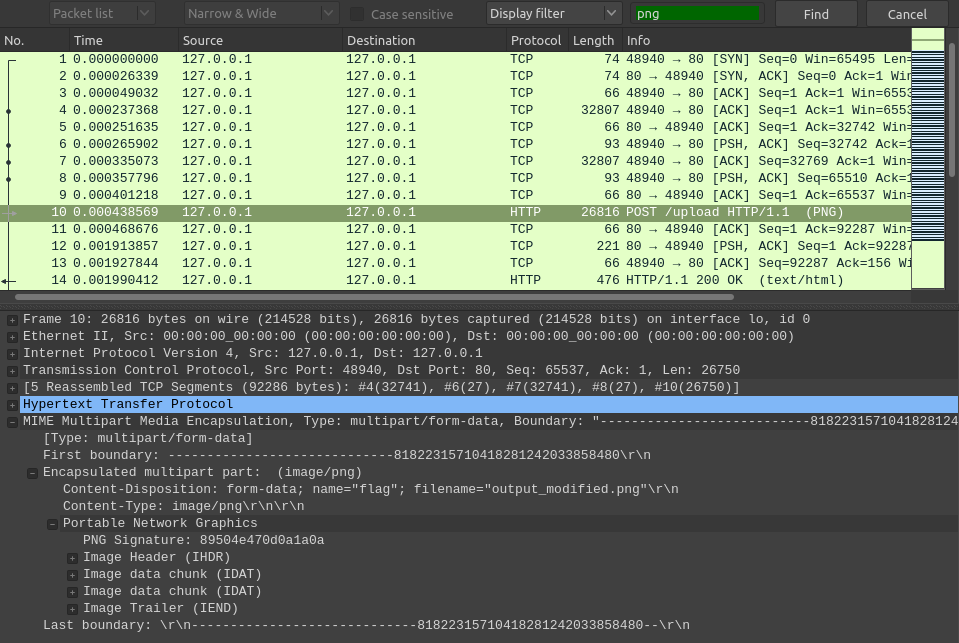
The challenge talks about photos being uploaded on random sites. So let’s find those images using the filter functionality in Wireshark (CTRL+F):
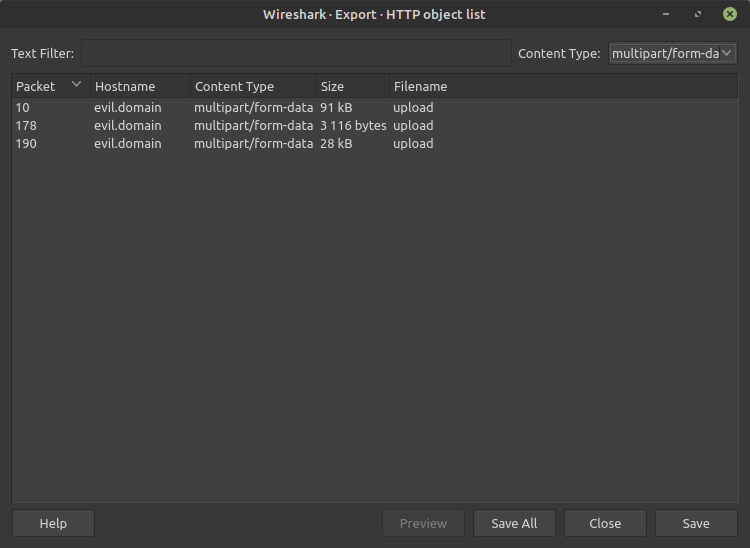
We found 3 PNGs and we export them (File -> Export Objects -> HTTP and Content-Typ: multipart/form-data for images only):
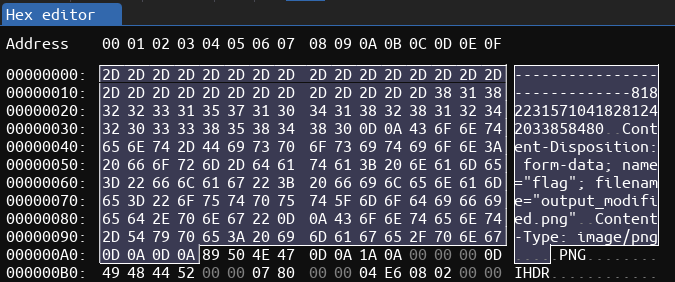
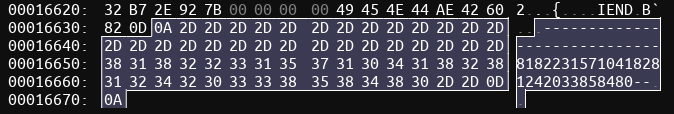
Now we have 3 “partial” PNGs because we still need to remove the form data boundaries (here with ImHex):
After we fix those 3 images, we can use steganography tools to find hidden data.
- We first used stegoVeritas to find any information in transformed images (LSB, RGB) but we cound not find any useful information;
Then we used zsteg to detect any stegano-hidden and we found something interesting:
1 2 3 4 5 6
$ zsteg -a 1.png imagedata .. file: MacBinary, Mon Feb 6 07:28:16 2040 INVALID date, modified Mon Feb 6 07:28:16 2040 "F" ... b4,g,msb,yx .. file: OpenPGP Public Key b8,g,lsb,yx .. text: "FCCTF{H1dd3n_d4t4_1n_p1x3ls_i5n't_f4n_4nd_e4sy_to_f1nd!}TFCCTF{H1dd3n_d4t4_1n_p1x3ls_i5n't_f4n_4nd_e4sy_to_f1nd!}TFCCTF{H1dd3n_d4t4_1n_p1x3ls_i5n't_f4n_4nd_e4sy_to_f1nd!}TFCCTF{H1dd3n_d4t4_1n_p1x3ls_i5n't_f4n_4nd_e4sy_to_f1nd!}TFCCTF{H1dd3n_d4t4_1n_p1x3ls_" ...
And this time we get the flag: TFCCTF{H1dd3n_d4t4_1n_p1x3ls_i5n't_f4n_4nd_e4sy_to_f1nd!}.