TFC CTF 2023 - MCTEENX
Description
- Category:
Forensic
I fly in the sky, I got wings on my feet.
Download:
Resolution
1. Break the ZIP
We have here a password protected ZIP file which contains a single file script.sh.
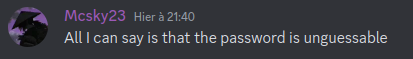
The first idea was to bruteforce the password but the creator of the challenge implied that it was impossible on Discord:
This saved us a lot of time.
Then there is another type of attack on ZIP files: Known plaintext attack.
I followed the writeups of LyMo1 who explained clearly how to conduct this attack.
We can recover the file inside an ecrypted ZIP file if we know at least 12 bytes of the file.
Since the file is a shell script and shell scripts often start with a shebang, we could use it as plaintext:
1
$ echo -n -e '#!/bin/bash\n' > plaintext
I added \n because the shebang is only 11 bytes and also we usually skip a line after it.
Now we use bkcrack to crack the ZIP:
1
2
3
4
5
6
7
8
9
$ bkcrack -C red.zip -c script.sh -p plaintext
bkcrack 1.5.0 - 2022-07-07
[19:48:26] Z reduction using 5 bytes of known plaintext
100.0 % (5 / 5)
[19:48:26] Attack on 1218664 Z values at index 6
Keys: c0b1bc78 c3206dfc e7e5bae1
88.7 % (1081137 / 1218664)
[20:16:18] Keys
c0b1bc78 c3206dfc e7e5bae1
It took us quite some time to get the key to recover the shell script:
1
2
3
4
$ bkcrack -C red.zip -c script.sh -k c0b1bc78 c3206dfc e7e5bae1 -d script.sh
bkcrack 1.5.0 - 2022-07-07
[20:17:04] Writing deciphered data script2.sh (maybe compressed)
Wrote deciphered data.
2. PNG Steganography
The script.sh seems to store a base64 encoded PNG:
1
2
3
#!/bin/bash
echo 'iVBORw0KGgoAAAAN[...]AASUVORK5CYII=' | base64 -d > red.png
We ran the script but we got a broken PNG:
1
2
3
pngcheck red.png
red.png this is neither a PNG or JNG image nor a MNG stream
ERROR: red.png
I tried to fix it by manually editing bytes but I didn’t succeed.
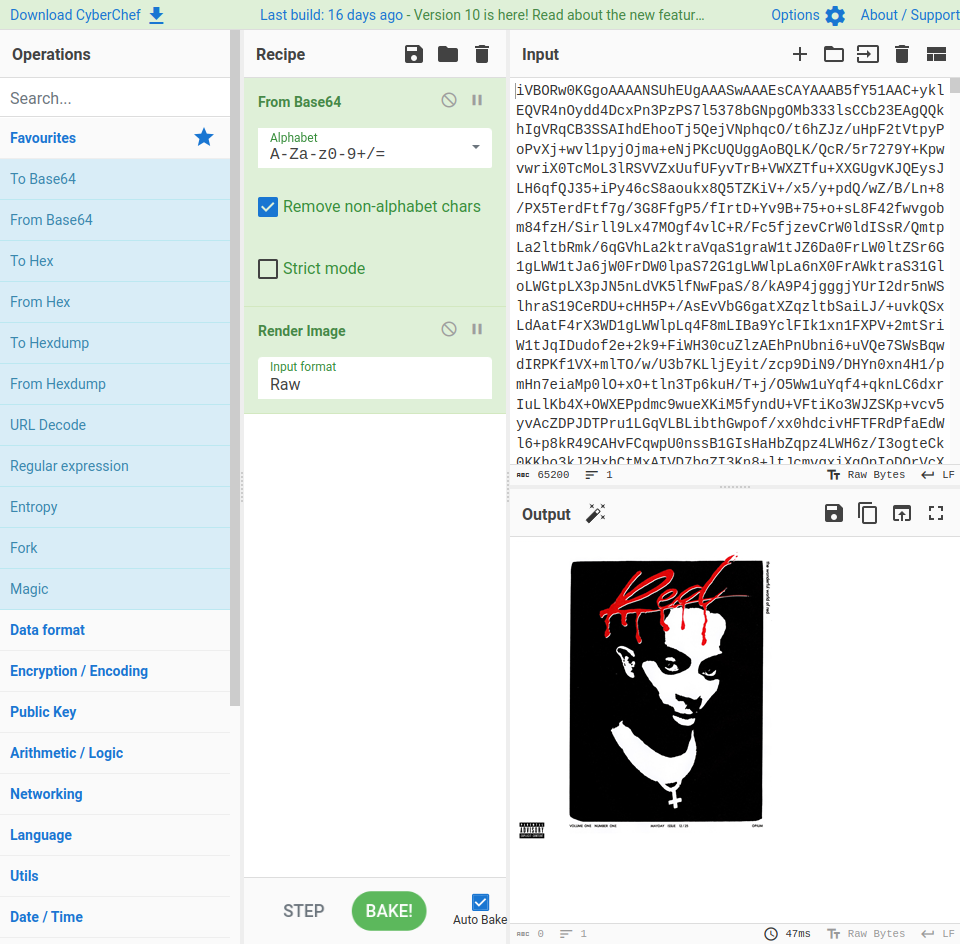
So I tried to decode the base64 with CyberChef and it worked:
There is nothing interesting in the picture so let’s run some steganography tools.
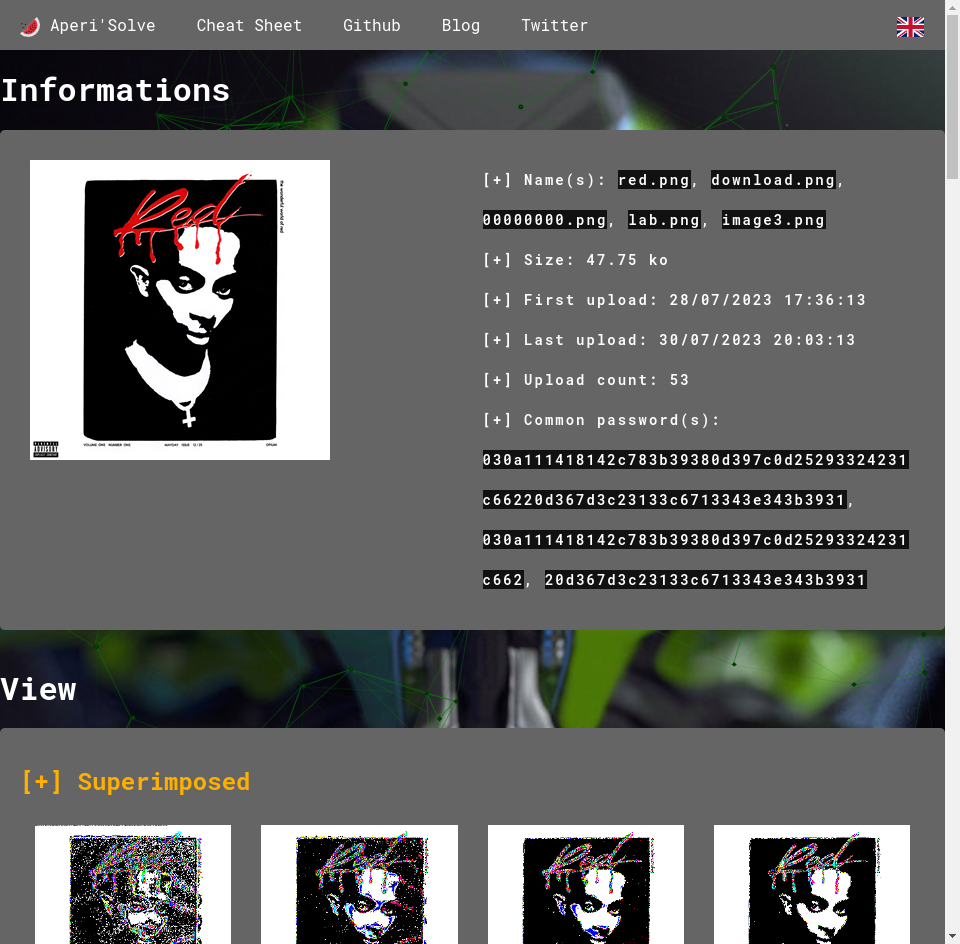
I used the web version of AperiSolve which is a great tool for steganography because it has a lot of tools embedded.
3. Break the cipher
We found an interesting hex strings (given by zsteg):
030a111418142c783b39380d397c0d25293324231c66220d367d3c23133c6713343e343b3931
Since we have no information about the encryption method of this hex string, we tried a XOR plaintext attack:
1
2
3
4
5
6
7
8
9
from pwn import *
cipherhex = "030a111418142c783b39380d397c0d25293324231c66220d367d3c23133c6713343e343b3931"
cipherbytes = bytes.fromhex(cipherhex)
plaintext = b"TFCCTF{"
print(xor(cipherbytes, plaintext)[:len(plaintext)])
This gave us b'WLRWLRW' and we can clearly see a repetition of the key WLR.
We use this key to decrypt:
1
2
3
4
5
key = b"WLR"
plaintext = xor(cipherbytes, key)
print(plaintext)
And we get the flag: TFCCTF{4int_n0_reasoN1n_a1nt_n0_fixin}.